Threat intelligence is undoubtedly one of the pillars of today’s security process management landscape. Leading institutions are constantly seeking to extend the boundaries of organisational visibility, to identify, predict and prevent the most likely incidents.
In governmental environments, APT (Advanced Persistent Threat) groups and other high-risk actors can spend months or even years destroying critical infrastructure, disrupting operations, and stealing sensitive information belonging to governments all around the world. These dangerous adversaries adapt and exploit advanced evasion techniques to bypass protective measures and repeatedly attack the same targets.
Threat intelligence is critical in dealing with such actors, and primarily involves the collection, collation, and distribution of information regarding threats that compromise the integrity and confidentiality of different institutional departments. To ensure that the outcome of any cyber intelligence process will yield data of value to all stakeholders, these threats must be identified and prioritised.
Honeykube utilises container isolation technology in Kubernetes to create custom honeypots, which are then combined to seamlessly replicate government infrastructure. This allows the rapid generation of an ideal analysis environment to attract high-profile malicious actors, revealing details of the strategies they are using against information assets.
APT groups use sophisticated methods to ensure a consistent level of stealth, by lateral movement, persistence, and information manipulation. This is often of vital importance in critical infrastructures, where maintaining presence and control over long periods of time is vital to the success of their malicious campaign. Unlike a real system where it can be difficult to separate anomalous patterns from normal system events, in a honeypot all activity is presumed to be malicious, allowing a clear and comprehensive view of the flow of events.
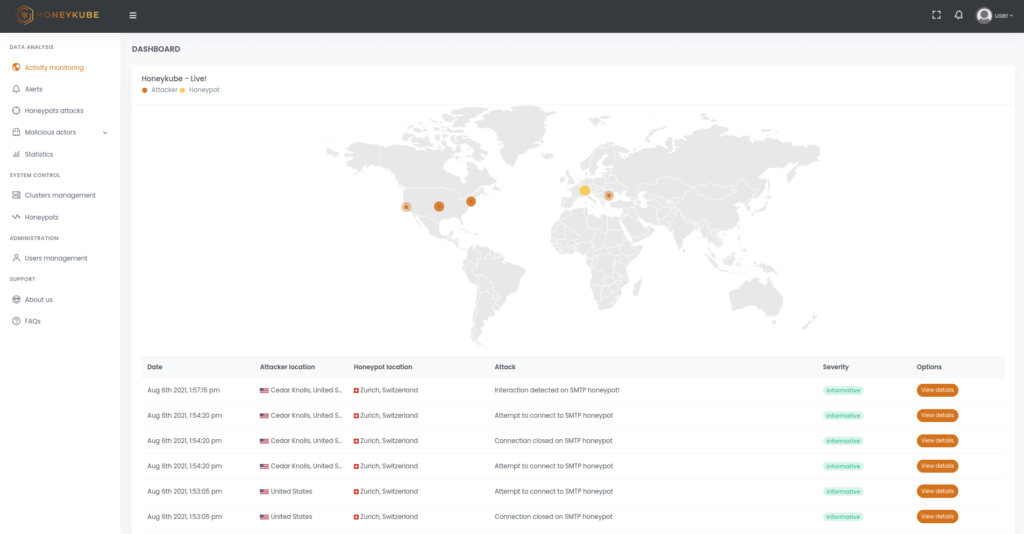
Image 1. View of real-time attacks in Honeykube.
As the Honeykube honeypots are highly customisable on a case-by-case basis, it is impossible for an attacker to determine whether they are on a real system or inside one of our honeypots. This makes it the ideal environment to analyse the development of malicious campaigns in real time. While the attacker uses different techniques to try to escalate permissions such as exploiting zero-days, executing malware, or making lateral moves to other services, Honeykube can record each of their activities as they occur.
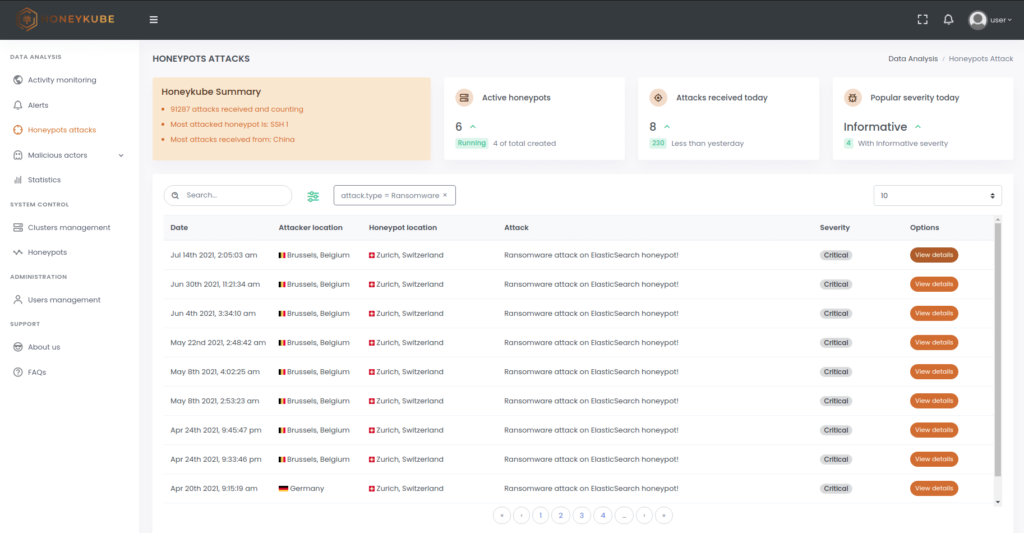
Image 2. Honeykube offers more than a dozen filters to quickly find the attacks of interest. For example, ransomware attacks can be rapidly identified using the attack type filter.
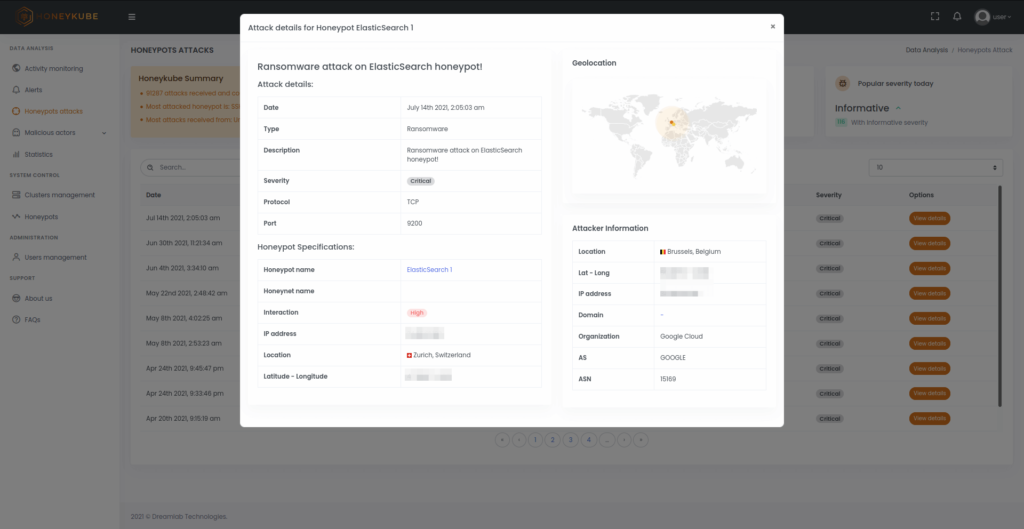
Image 3. Details of a ransomware attack, showing information about the malicious action detected, the source IP and the honeypot that has been affected.
Our solution was designed to track, geo-locate and reveal the mechanisms used by malicious actors, enabling advanced profiling of adversaries with details on their preferred attacks, tools, tactics, techniques, and procedures. Being able to perform advance detection of the compromise techniques being used, allows weaknesses in the security infrastructure to be identified and reviewed.
Honeykube allows authorities to visualise the attacks being carried out against the different honeypot clusters in real time. The most frequent types of attacks, their severity and country of origin, and which services have attracted the greatest interest from adversaries, are all quickly identified.
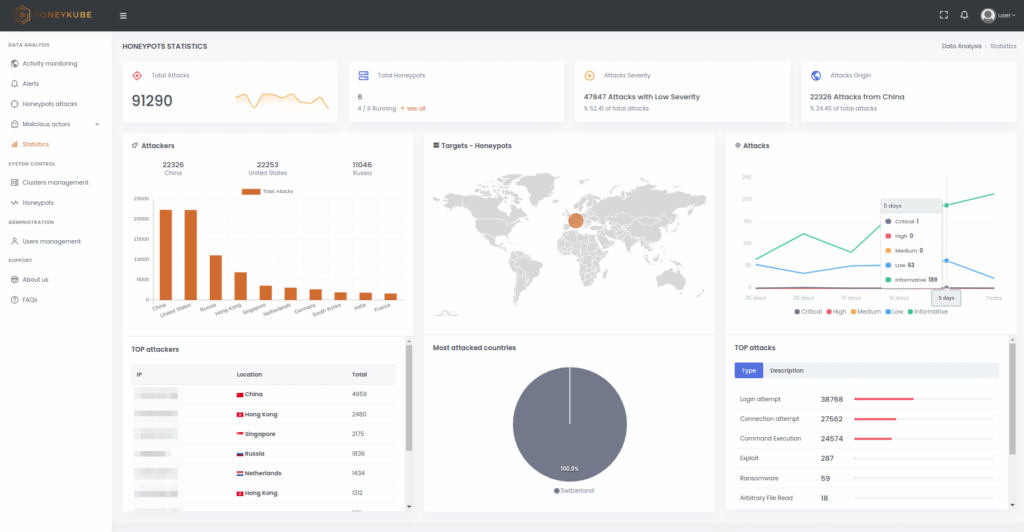
Image 4. Statistics panel in HoneyKube.
The profiling section can identify the attackers showing real interest in the honeypots, separating them from simple exploratory scripts and providing a summary of their interactions with the different services deployed.
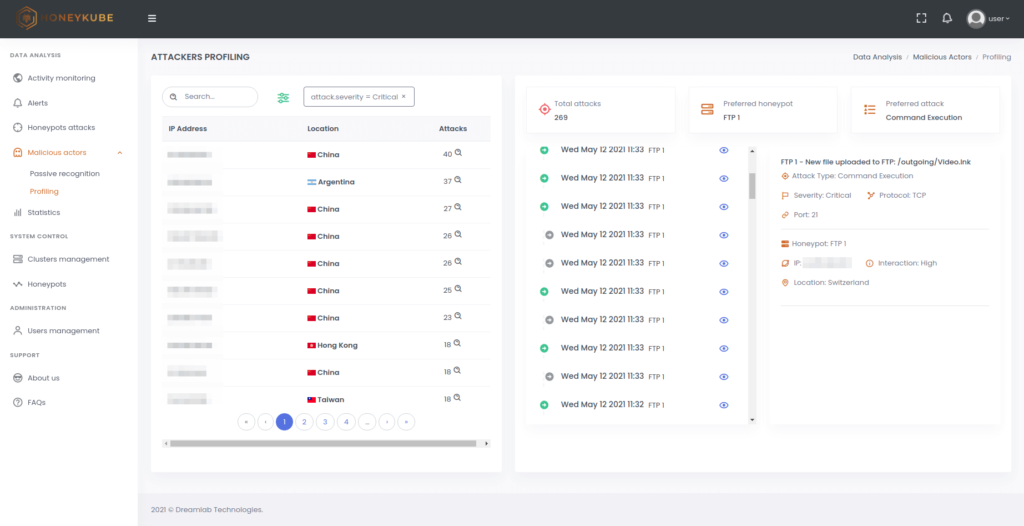
Image 5. Attackers profiling in Honeykube.
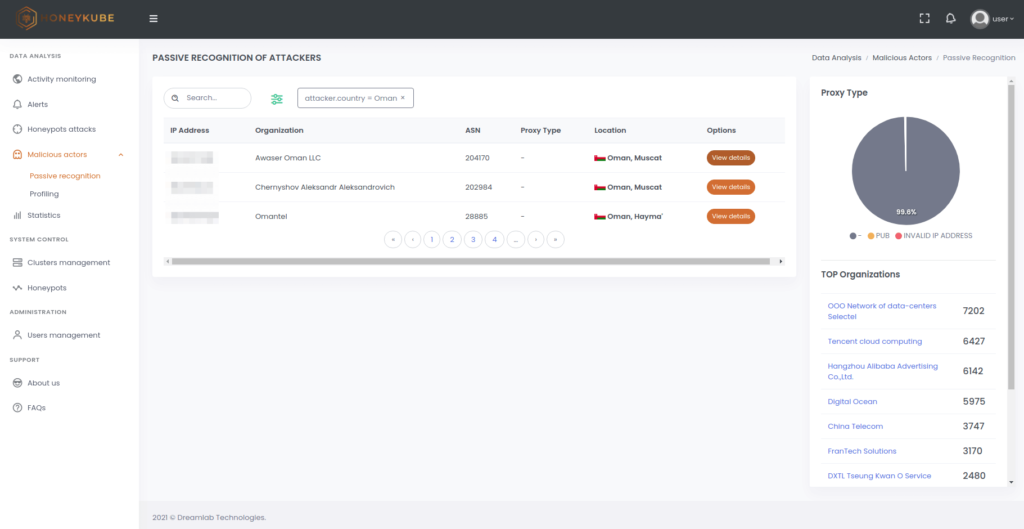
Image 6. Quickly display details of the malicious connections that your honeypots are receiving.
Conducting a threat assessment allows different organisational units to identify and prioritise key threats and the actor groups behind them. Understanding who is likely to target the organisation and how they are likely to do so, provides vital information, helping to inform the enhancement of security strategy.
Of course, it is not only public institutions that can find indicators of compromise linked to APT groups, and the mere existence of such indicators may be insufficient proof that the system is being targeted by known adversaries. Regardless, the ability to detect such attempts and to determine how they fit into the prevailing geopolitical agenda will be key instrengthening strategy when pursuing improved national security.