Detect, capture and analyse
advanced cyber-attacks
in
real-time with ease
Detect, capture and analyse
advanced cyber-attacks
in real-time with ease
FOR ADVANCED CYBER DEFENSE
Honeykube is an innovative threat intelligence platform for honeypot and honeynet management and sophisticated adversary analysis. It combines traditional deception techniques with advanced data collection and
Honeykube is an innovative threat intelligence platform for honeypot and honeynet management and sophisticated adversary analysis. It combines traditional deception techniques with advanced data collection and automated analytics, offering real-time and user-friendly dashboards and reports on the tactics, techniques and procedures of cyber-attackers, enabling organisations to focus on higher value activities.
automated analytics, offering real-time and user-friendly dashboards and reports on the tactics, techniques and procedures of cyber-attackers, enabling organisations to focus on higher value activities.
ACTIONABLE CYBER INTELLIGENCE
Honeykube removes the time-intensive process of building and maintaining complex infrastructures by contextualising collected data to generate business-ready dashboards and reports which are ready to act upon.
ARMING SECURITY CONSCIOUS ORGANISATIONS WITH THE RIGHT TOOLS
Honeykube allows your security team to deploy and manage honeypots all around the world either on a pre-built or on-demand basis. Honeykube uses next-generation technology that overcomes all the barriers and limitations associated with traditional honeypots.
- For government bodies and military forces
- For critical infrastructures providers
- For threat hunters and threat research and intelligence specialists
- For security-conscious industries and organisations that rely on an operational, secure, and resilient environment
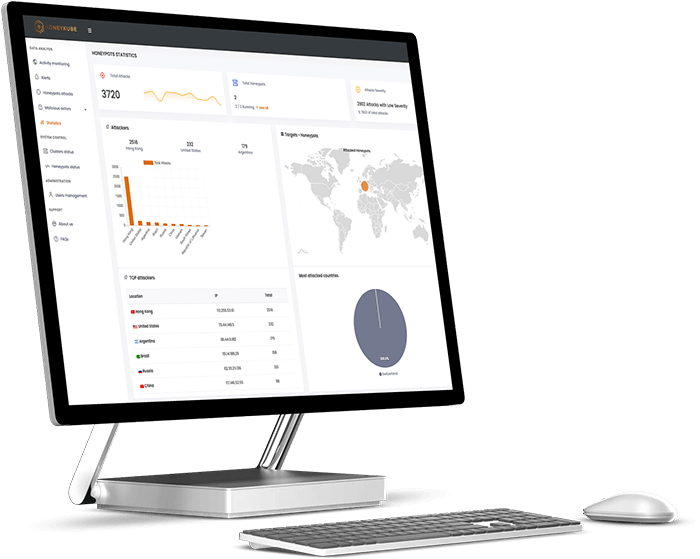
A NOVEL APPROACH TO HONEYPOT DESIGN
Honeykube is the first honeypot solution fully-managed by Kubernetes, providing robust isolation layers and advanced functionality and management features. This container technology guarantees the resilience of honeypots and quality of information collected. It can be installed on-premises, in the cloud or provided as a service.
KEY FEATURES AT GLANCE
Highlights risks to the management team of the scale and severity of the threat
Provides detailed assessments based on the attacker’s methods and techniques
Supports forensic investigations and incident response planning
Gathers valuable and uninterrupted threat intelligence
Enables continuous monitoring and analysis of threats and malicious actors in real time
SEE HONEYKUBE IN ACTION
To see how Honeykube could save your company resources and increase your threat Intelligence, schedule a free demo with our experts that are always available to understand your needs.
Our experts will walk you through the features and processes of our intelligent solution and demonstrate how you can integrate them into the security tools that your researchers and network operators use.
FAQ
- Emulates your organisation infrastructure to expose the adversaries who are interested and the techniques they will use against you.
- Shows real-time visualisation of attacks, enriched with information for advanced analytics.
- Provides a fine-grained alerting system based on attack severity.
- The comprehensive set of dashboards help make sense of all data processed by the analytics engine, providing deeper insight into your business whilst saving investigation time.
- Launch real honeypots for web servers, file servers, database servers, network devices, industrial systems, medical devices and IoT devices, amongst many others.
- Manage honeypots and honeynets deployed in different countries all around the world.
- A concise and user-friendly interface for streamlining honeypots management. Start, destroy, restart and scale honeypots with just one click.
- Traces, geolocates and reveals the techniques used by malicious actors. Advanced adversary profiling with details about their preferred attack, tools, tactics, techniques and procedures
- Ability to emulate from simple to complex infrastructures like hospitals, power plants and other critical infrastructures.
- Honeypots that look like real assets from the attacker’s perspective.
- Honeynets with several honeypots to analyze attacker’s lateral movements.
- Kubernetes-managed honeypots which provides robust isolation layers and practical management features.
- Support of multiple clusters of honeypots from different Cloud providers and on-premise installations.
- Powerful analytics engine to process the attacks and show detailed information, saving a lot of time to analysts.
- Powerful tracking system of malicious actors.
- Complete dashboard of statistics to easily view the most relevant information.



