In recent years, the quantity, diversity and complexity of malicious code has increased dramatically. This has been further fuelled by the recent rise of teleworking, with attackers intensifying their focus on developing campaigns aimed at major corporate targets. There are millions of new malware samples arriving in analysis labs each day, with new tools constantly expanding the repertoire of methodologies used by attackers.
In addition to the ever-present zero-day exploits, new fileless malicious execution techniques via binaries and scripts – commonly referred to as “living off the land” – add to the complexity of anticipating and detecting targeted campaigns. As a result, the ability to monitor and quickly visualise anomalous behaviour within the system has never been more important. In parallel, adopting a proactive posture that reaches beyond the analysis of security incidents and instead focuses on cyber threat intelligence, becomes critical. In this context, understanding the ecosystem of malicious actors in which the target system is immersed, is key to properly protecting information assets.
The rise of new tools such as MITRE ATT&CK among researchers around the world, serves to highlight the direction in which security management processes are evolving. The ability to correlate the techniques and tactics observed in security incidents with specific APT (Advanced Persistent Threat) groups, geographic regions, and industries, becomes a mechanism that not only allows attacks to be prevented, but also allows the prediction of the likely course for exploitation attempts on the networks themselves.
Honeykube was designed with cyber intelligence in mind. Combining the best features of traditional honeypots and the full potential of containers in Kubernetes, our solution allows you to quickly deploy honeynets with different levels of interaction, capable of seamlessly representing your corporate infrastructure. Taking advantage of cloud environments, it is possible to start, stop and restore honeypots in different countries around the world with a single click.
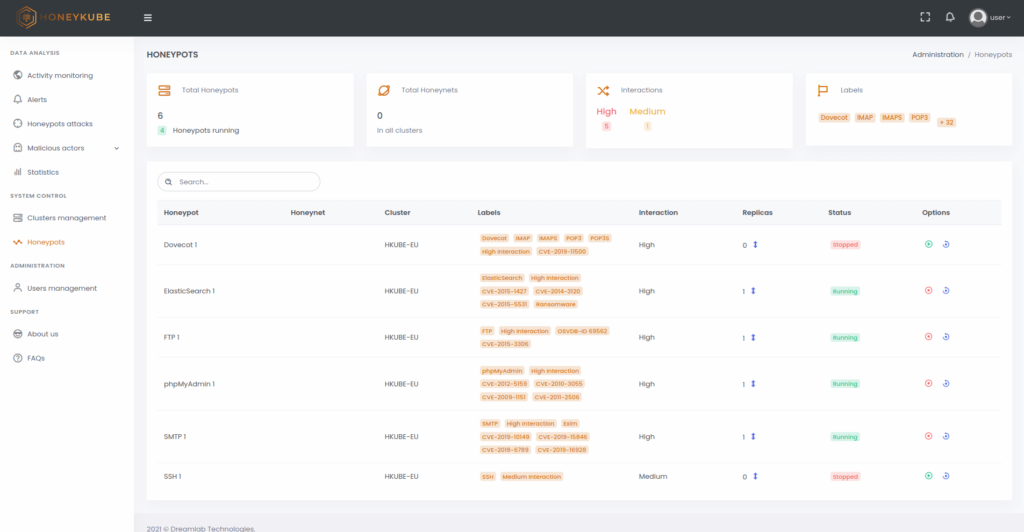
Image 1. Starting, stopping and restoring honeypots are simple actions from the Honeykube control panel.
Our solution was created for either organisations or independent analysts who wish to gain an in depth understanding of the types of attacks targeted at specific services or infrastructures, as well as the profile of the actors behind them. The versatility of the technology behind Honeykube allows not only the recreation of a corporate infrastructure, but also the recording of all connection attempts, vulnerability exploitation, malware execution, privilege escalation, lateral movement, information exfiltration, or any other action that an attacker might perform inside the equipment.
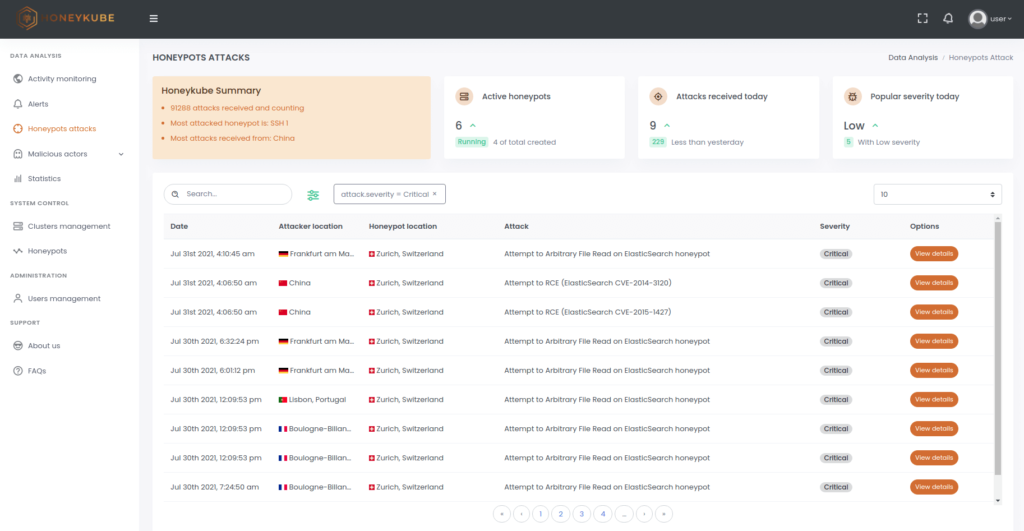
Image 2. Honeykube offers more than a dozen filters to quickly find attacks of interest. For example, critical attacks are quickly identified using the severity filter.
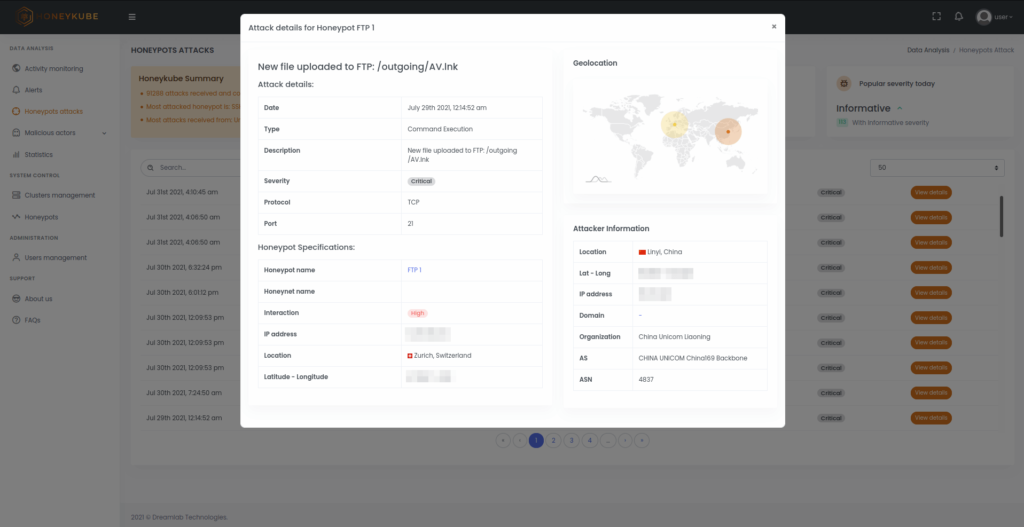
Image 3. Details of a critical attack, where information of the malicious action detected, the source IP and the honeypot that has been affected can all be seen.
The ability to customise the services of each honeypot to more accurately simulate real systems, is coupled with the ability to use highly interactive honeypots built around services running – in isolation – inside containers that appear completely legitimate from the attacker’s perspective. This combination helps to create an analysis environment that dramatically increases the likelihood of quickly attracting malicious actors of interest.
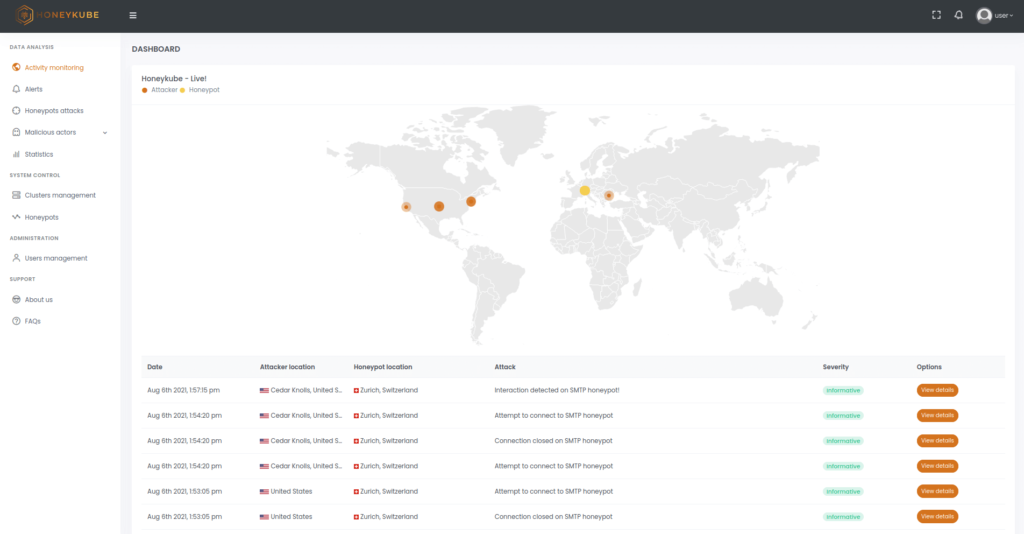
Image 4. View of real-time attacks in Honeykube.
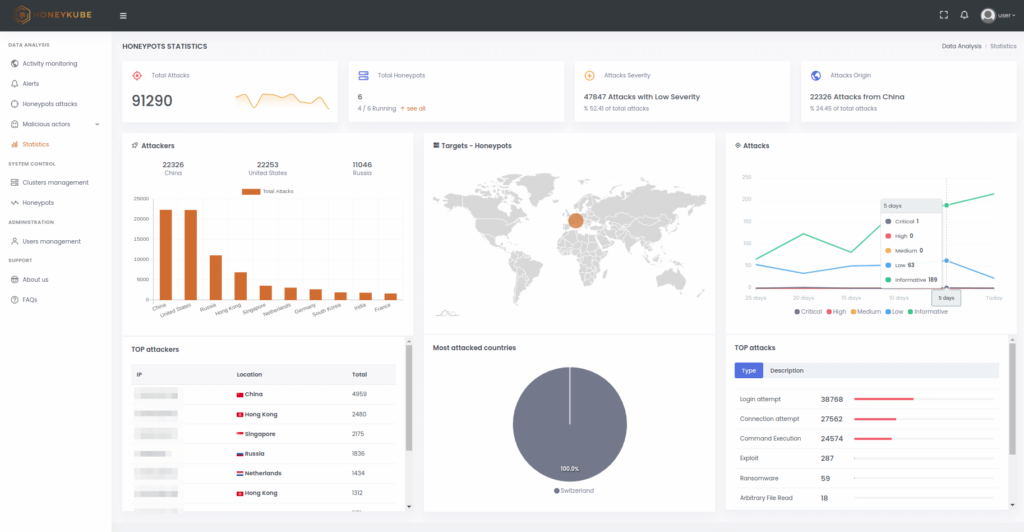
Image 5. Statistics panel in Honeykube.
In addition, the profiling section allows the rapid identification of any attackers showing a real interest in the honeypots, separating them from simple exploratory scripts and providing a summary of their interactions with the different services deployed.
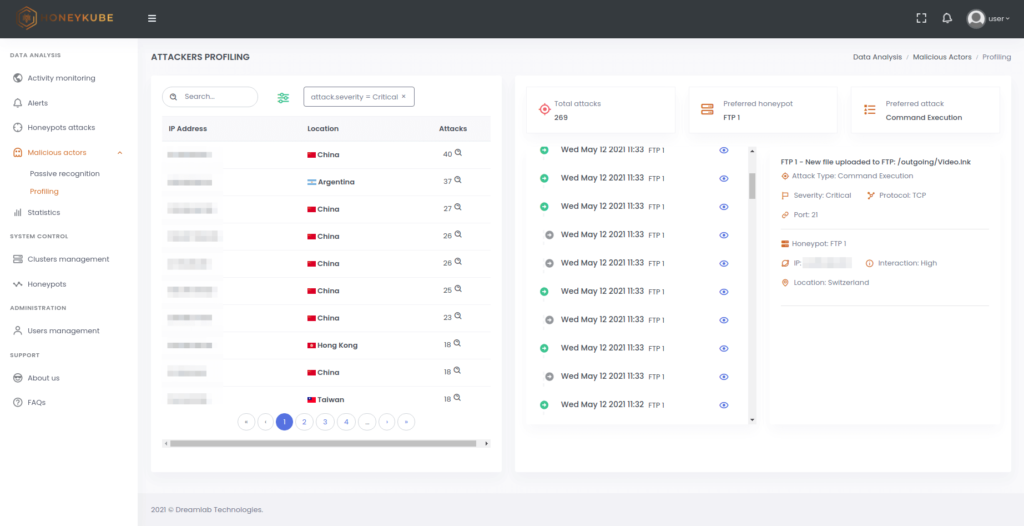
Image 6. Attacker profiling in Honeykube.