Honeykube is different from other solutions on the market due to its incredible adaptability, versatility to recreate all types of IT infrastructures, and resistance to detection from the attacker’s viewpoint. The following describes some of the technology that powers our cyber threat intelligence solution.
In the IT world, containers aren’t simply a novelty tool. Naturally, the idea of being able to contain the execution of a sample of malicious code to study its behaviour, is particularly attractive in the field of information security. Since the introduction of this principle in sandboxing environments, virtual machines, honeypots, or cloud infrastructures, analysts have used the ability to isolate the execution of processes both to protect information assets and to study the behaviour of attackers.
The container landscape has clearly taken a new course since the expansion in popularity of Docker and Kubernetes. In recent years, Kubernetes has shaped the cloud infrastructure scene, becoming the flagship platform for managing cloud environments through robust isolation layers and easy-to-use, versatile container management tools.
Kubernetes was designed with the idea of generating stable deployments and maintaining high availability in complex systems. It provides robust isolation layers and mechanisms to link containers in complex structures, compatibility with various cloud providers allowing the implementation of containers around the world and offering a platform to run a myriad of services. As a result, Kubernetes was the best choice for designing our on-demand honeynets solution, allowing real-time threat analysis.
Combining container technology with the best features of traditional honeypots, Honeykube allows you to design custom services, with levels of interaction specifically tailored to meet the requirements of your business.
On one hand, there are low-interaction honeypots. These allow the attacker to interact in a limited way with the operating system, usually emulating a small subset of protocols and functions. This type of honeypot is easily identifiable, as the attacker is unable to perpetrate complex attacks, such as exploiting zero-days, executing malware, or performing lateral movement to other machines. However, they do have many advantages: they are quick to develop, easy to maintain, require fewer resources and can be used to identify exploratory malicious activity on the network.
On the other hand, we have high-interaction honeypots that act as a decoy by making real systems available to the attacker. In this case, it is no longer a mere emulation, but a complete system where the attacker can explore their full range of tools, seeking to compromise and secure persistence on the system. Any attempt to connect, exploit, execute malware, escalate privileges, lateral movement, exfiltrate information or other technique, will be logged, allowing the analyst to generate a complete profile of the attacker’s behaviour. Although these honeypots take longer to develop and consume more resources, they provide vastly superior advantages in profiling the risks to which the organisation is subject.
Between low- and high-interaction honeypots, there is a complete spectrum of decoy systems with different degrees of interaction. These allow for deeper emulation of certain services and technologies and can be used to analyse attackers’ behaviour in the face of specific vulnerabilities. The versatility of containers means that you are limited only by your own imagination
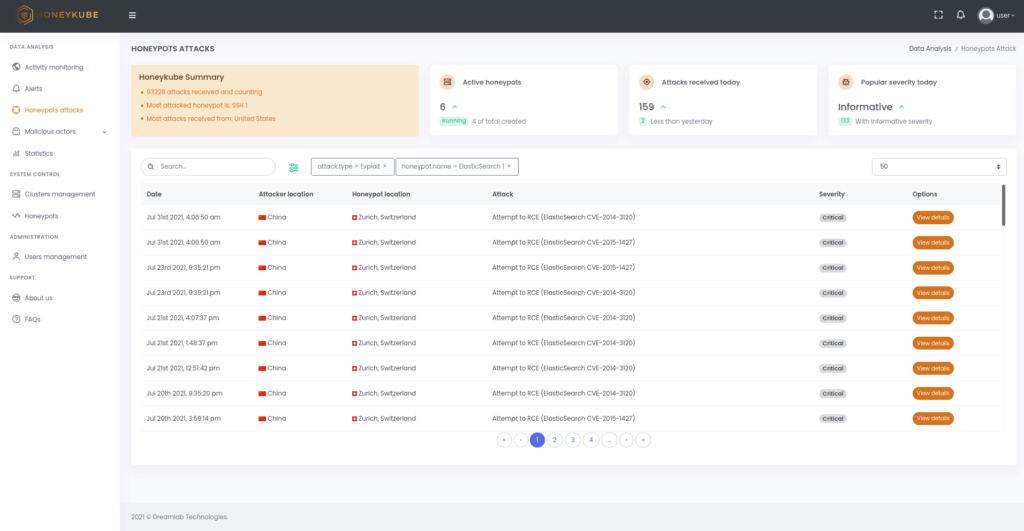
Figure 1. Honeykube offers more than a dozen filters to quickly sort and find relevant attacks. For example, you can quickly search for exploit attacks targeting specific honeypots.
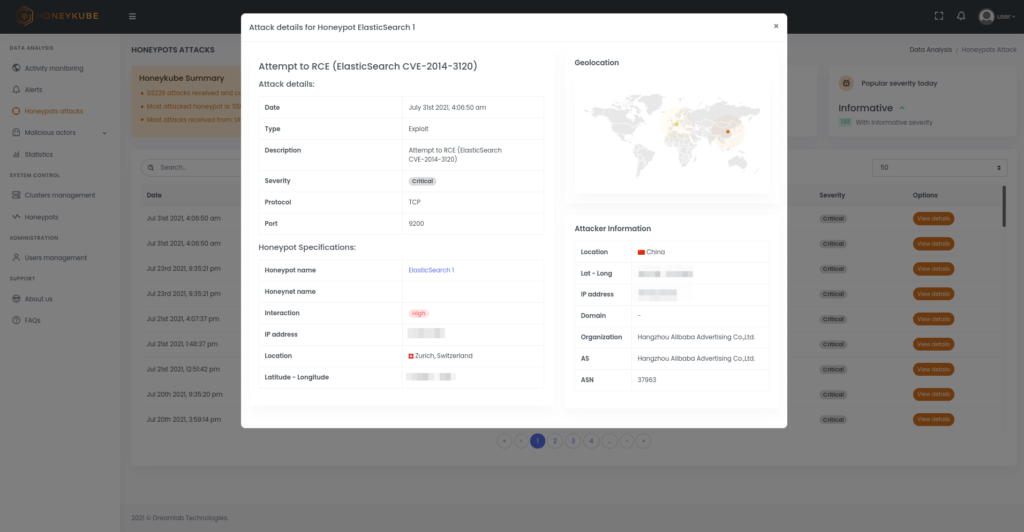
Figure 2. Details of a critical attack, where one can observe information of the malicious action detected, the source IP and the honeypot that has been affected.
The real flexibility of Honeykube lies in the fact that, if it can be run in a container, it can become a honeypot. Web servers, file servers, database servers, network devices, industrial systems, medical and IoT equipment – the list is endless. In truth, the resources available in terms of development time and maintenance cost will be the real limiting factors when designing honeypots.
Moreover, Kubernetes offers the flexibility to combine different containers and create complex infrastructures, replicating the exact corporate infrastructure. This allows analysis environments to be created, to detect and study advanced attacks, and obtain a clear picture of which exploitation vectors are most used by attackers as they try to compromise the systems. The results facilitate the customer in strengthening the protection measures implemented, based upon the actual behaviours observed in attacks against their Honeykube systems.
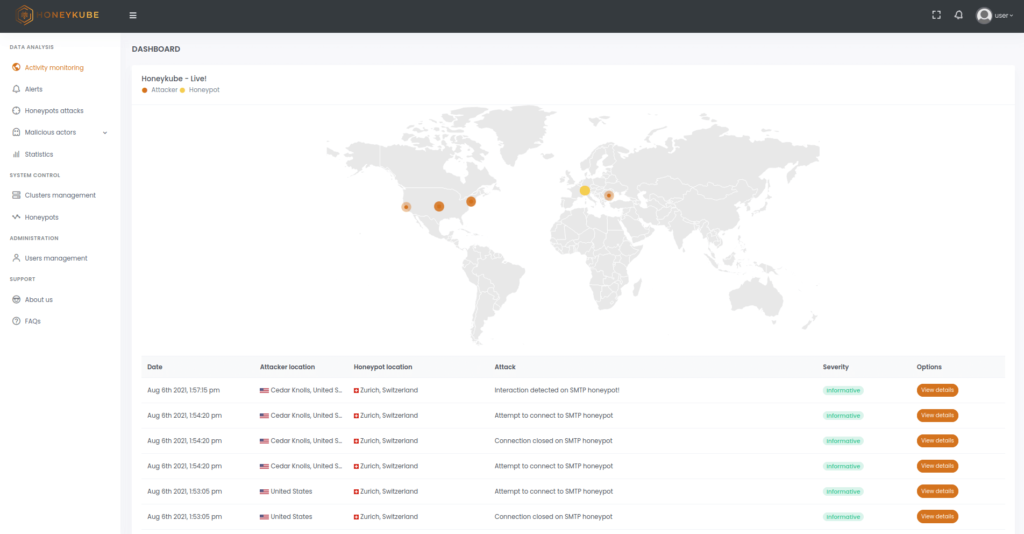
Figure 3. View of real-time attacks in Honeykube.
Through a robust cloud architecture supported by Google Cloud Provider, Honeykube allows honeynets to be deployed in different countries, depending on the industry, geographic location of the operations centres, or region of interest to the analysts. It is also possible to utilise and manage local or third-party cloud provider-based installations as required by the organisation.
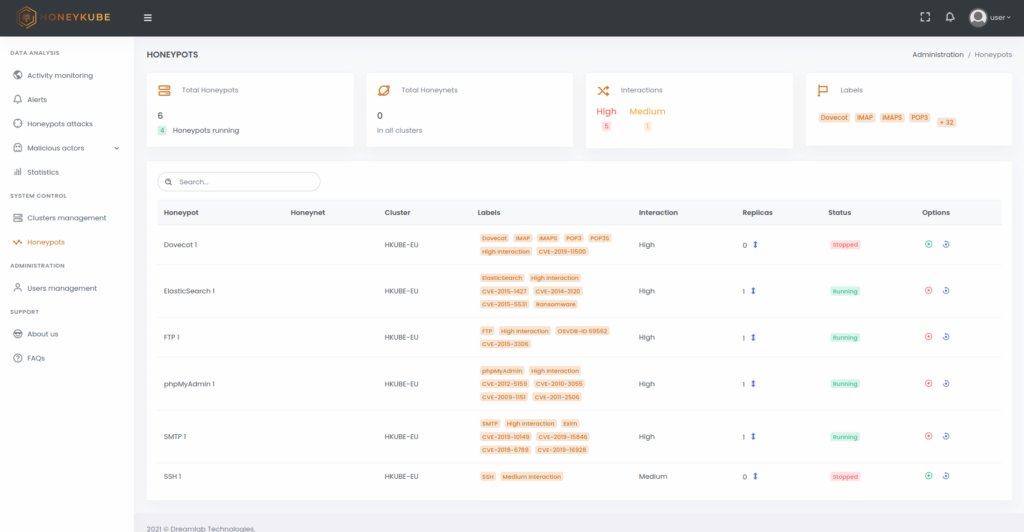
Figure 4. Starting, stopping and restoring honeypots is very simple from Honeykube’s control panel.
Leveraging the ease of deployment of containers, Honeykube enables honeypots to be started, stopped, or restored with a single click, removing any trace of malicious activity in a compromised environment, and rapidly making it ready to respond to any new attack.
Honeykube can become a critical asset in the collection, distribution, and presentation of information regarding key threats to your organisation and the adversaries driving them. It will facilitate and reduce analysis time in cyber intelligence processes and provide critical information for security system improvement.